by Kappy Prasad | Feb 9, 2015 | Articles, Blog, Linux, Technical
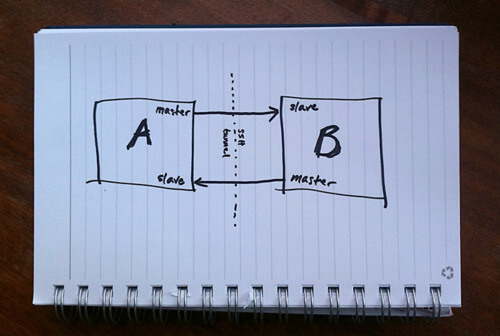
MySQL Replication is incredibly simple to get up and running and this post will instruct you through it. Simple Master -> Slave Replication MySQL allows you to build up complex replication hierarchies, such as multi-master, chains of read slaves, backup databases at a remote site or any combination of these. This article focuses on a simple single master to single slave setup. This article also assumes that 2 MySQL Servers have been installed but that there is no existing data in the master that needs to be copied to the slave – it’s not complex to add that extra requirement and it will be covered in a future post. Server “masterhost” (192.168.0.31) is to be our master and “slavehost” (192.168.0.34) the slave. Step 1: Edit the configuration files & start the MySQL Servers The first step in setting up replication involves editing the “my.cnf” file on the servers that will serve as the master and slave. A default is provided with the MySQL installation but in case there is already a production MySQL database running on these servers, we provide local configuration files “master.cnf” and “slave.cnf” that will be used when starting up the MySQL servers. At a minimum we’ll want to add two options to the [mysqld] section of the master.cnf file: log-bin: in this example we choose inodecloud-bin.log server-id: in this example we choose 1. The server cannot act as a replication master unless binary logging is enabled. The server_id variable must be a positive integer value between 1 to 2^32 master.cnf: [mysqld] server-id=1 log-bin=black-bin.log datadir=/home/inode/mysql/master/data innodb_flush_log_at_trx_commit=1 sync_binlog=1 Note: For the greatest possible durability and consistency in...

by Kappy Prasad | Jan 21, 2015 | Articles, Blog, Linux, Technical
If you’re a developer or work in IT, you’ve likely heard of Docker. It’s a 3 year old open source technology that has grown exponentially during its existence. And now, it’s beginning to turn heads in even the most regulated industries. First let’s explore what Docker actually is for those that are unfamiliar. “Docker is an open platform for developers and sysadmins to build, ship, and run distributed applications,” according to the Docker website. The technology consists of two tools, the Docker Engine and the Docker Hub. The Docker Engine is a, “portable, lightweight runtime and packaging tool,” while Docker Hub is a, “cloud service for sharing applications and automating workflows.” The technology is particularly appealing for developers because it is now easier than ever to make sure you develop, test and deploy using the same environment as your colleagues, resulting in less issues caused by differences or missing libraries. Docker also offers developers the flexibility to quickly run their apps anywhere, whether its on laptops, VMs or QA servers. More simply put, “Docker helps developers build and ship higher-quality applications, faster.” Sysadmins are finding the technology useful as well, because of the ability to standardize development environments among other reasons. “Docker helps sysadmins deploy and run any app on any infrastructure, quickly and reliably.” Docker seems to be on the same disruption path as GitHUB, which shook the source control systems, or more lately, how composer “revolutionized” the way we deploy components of a PHP and Symfony application. On the business side, the benefits may be huge. By simplifying the way we deploy apps and creating more manageable...

by Kappy Prasad | Jan 19, 2015 | Articles, How To's, Linux, Technical, Wordpress
With WordPress powering 61% of CMS based websites, it has become a lucrative target for hackers. Google blacklisting for phishing and email blacklisting for spamming is quite common in WordPress hosting. A well maintained WordPress site is immune to hacking, but in shared hosting, the majority of WordPress websites will be un-patched, and vulnerable to hacking. Through a few simple strategies, it is possible to make WordPress immune to hacking. Securing the web server through web application firewalls The efficiency of a web application firewall largely depends on how quickly the firewall is able to include zero day WordPress exploits into their signature database. While commercial signatures gave close to 100% detection rates, free rules from Comodo, AtomiCorp, etc for the mod_security Apache module is good enough to prevent more than 95% of exploit attempts. Additionally, we were able to extend the malware detection capability of mod_security module by integrating it with ClamAV anti-virus software. Enabling auto-upgrade for WordPress installations Since WordPress v3.7, automatic security updates are switched on by default, and wouldn’t break anyone’s site. We further extended this feature by plugins like Advanced Automatic Updates, which can upgrade plugins and themes as well. For customers who chose security over extensive customization, the full-auto-upgrade worked very well in preventing website exploits. File upload scanning through FTP Compromised FTP accounts are another major source of malware uploads. Desktops, laptops and mobile devices get infected with trojans all the time, and web masters losing their FTP login details are a common cause of malware uploads. We put a block on this channel by deploying file upload scanners. For those web hosts...

by Kappy Prasad | Dec 20, 2014 | Articles, How To's, Linux, Technical
You may find yourself often fighting the frustration of having your business emails getting classified as spam in your customer email boxes. The fact is that about 80-90% of ALL email on the internet is spam. In spite of this, businesses anticipate increasing the number of email campaigns on the web. To stop the bombardment, people and businesses are creating filters, or buying company services that filter email so that they receive only content that they deem relevant to them. So, whether or not your email is legitimate, if a receiving host or email spam program is aggressive or set a certain way, your emails could very easily get marked as spam. Unfortunately, this is not a server or hosting issue. This is a general issue with email that you will find no matter where you host your business emails. This article discusses what you can do from your end. Steps to take when your emails are marked as spam There are several things that may help, but bear mind these are suggestions and not a guarantee that your email will no longer be filtered as spam: Make sure that you are not in violation of the CAN-SPAM Act of 2003. Verify that your emails make the grade and you’re not falling into common filtering rules. Send your customers a personal email message requesting that they white-list your domain, so that your business emails don’t get filtered into Spam. In this, I’m referring to a “personal” email as one that doesn’t include your marketing links or business advertisements or enhancements that may flag the email as something other than a personal email. Check...

by Kappy Prasad | Dec 14, 2014 | Articles, How To's, Linux, Technical
Recently a client asked us about a problem they were having with email that was being run on the same server that we had setup their website on. In this case the problem was pretty severe as they had been blacklisted from sending emails to any Gmail.com email address. After contacting the hosting company we were able to identify that one of their email accounts had been compromised and was being used to send out SPAM emails. It was an unfortunate situation that could have been avoided. In this post we cover what blacklisting means, what to do, and how to avoid it from happening again. What does ‘blacklisted for email’ mean? Blacklist definition According to google.com a blacklist is ‘a list of people or products viewed with suspicion or disapproval.’ In regards to email to be blacklisted means a provider such as Google has determined that your domain is abusing its system by sending too many emails to addresses on its network. Once you have been added to a blacklist all emails you attempt to send to the provider will be denied and you will see a message similar to this one: SMTP error from remote mail server after end of data: host aspmx.l.google.com [74.125.142.27]: 550-5.7.1 [YOUR IP ADDRESS HERE 1] Our system has detected an unusual rate of 550-5.7.1 unsolicited mail originating from your IP address. To protect our 550-5.7.1 users from spam, mail sent from your IP address has been blocked. 550-5.7.1 Please visit http://www.google.com/mail/help/bulk_mail.html to review 550 5.7.1 our Bulk Email Senders Guidelines. ck6si8779257igc.40 - gsmtp How did you get blacklisted for email? You will...

by Kappy Prasad | Sep 26, 2014 | Articles, Blog, Linux, News, Technical
Yesterday we swiftly patched all of our customers web servers due to a critical vulnerability to Bash, aka the Bourne-Again Shell. but what damage could this vulnerability do? The flaw involves how Bash evaluates environment variables. With specifically crafted variables, a hacker could use this hole to execute shell commands. This, in turn, could render a server vulnerable to ever greater assaults. By itself, this is one of those security holes where an attacker would already need to have a high level of system access to cause damage. Unfortunately, as Red Hat’s security team put it, “Certain services and applications allow remote unauthenticated attackers to provide environment variables, allowing them to exploit this issue.” The root of the problem is that Bash is frequently used as the system shell. Thus, if an application calls a Bash shell command via web HTTP or a Common-Gateway Interface (CGI) in a way that allows a user to insert data, the web server could be hacked. As Andy Ellis, the Chief Security Officer of Akamai Technologies, wrote: “This vulnerability may affect many applications that evaluate user input, and call other applications via a shell.” That could be a lot of web applications — including many of yours. The consequences of an attacker successfully exploiting this vulnerability on a Web server are serious in nature. For example attackers may have the ability to dump password files or download malware on to infected computers. Once inside the victim’s firewall, the attackers could then compromise and infect other computers on the network. Aside from Web servers, other vulnerable devices include Linux-based routers that have a Web interface...







